Overview
App Services uses a range of network security protocols to prevent unauthorized access to your data. You can:
Configure TLS to secure network requests to and from your application.
Define IP addresses from which all outbound requests originate.
Define and manage URLs and IP addresses from which inbound requests may originate.
Transport Layer Security (TLS)
App Services uses TLS 1.3 to secure all network requests to and from your application, including:
Apps that connect from a Realm SDK.
Data API requests sent over HTTPS.
Queries and operations on a linked MongoDB Atlas data source.
The TLS certificate is pre-defined and cannot be customized or disabled.
Note
Backend Encryption
All internal communication between App Services and Atlas is encrypted with x509 certificates.
Firewall Configuration
App Services only sends outbound requests from a set list of IP addresses. The exact list depends on the cloud provider that the app server is deployed to. You can copy the IP addresses listed in this section to an allowlist for incoming requests on your firewall.
You can download a computer-friendly list of all IP addresses used by App Services in JSON or CSV format. You can also find cloud-provider-specific JSON and CSV files in the following sections.
Note
If you run a function from the Atlas App Services UI, the request originates from the server nearest to you, not the region the app is deployed to.
AWS
Download AWS IP Addresses: JSON, CSV
Outbound requests from an app deployed to AWS will originate from one of the following IP addresses:
13.236.189.10 18.202.2.23 18.210.66.32 18.211.240.224 18.213.24.164 52.63.26.53 54.203.157.107 54.69.74.169 54.76.145.131 18.192.255.128 18.157.138.240 18.158.38.156 52.220.57.174 18.140.123.126 13.251.182.174 65.0.112.137 3.6.231.140 13.234.189.107 13.232.212.70 65.0.113.75 3.7.215.88 3.6.255.136 65.0.188.79 13.233.17.88 18.136.226.22 122.248.203.228 54.251.109.67 54.255.78.248 54.179.247.236 13.251.170.158 3.105.146.190 52.65.242.206 54.79.24.107 13.238.106.70 52.28.11.211 3.121.9.73 52.29.205.189 3.122.49.121 3.121.58.147 3.121.97.130 108.128.63.52 108.128.66.245 108.128.51.69 108.128.45.118 52.213.157.241 108.128.66.107 3.9.6.254 3.9.74.211 3.9.61.59 35.176.121.115 3.9.85.190 3.9.47.47 13.36.132.152 15.188.240.49 13.37.29.138 15.188.152.56 13.39.52.19 15.188.159.135 177.71.159.160 52.67.231.12 18.230.146.14 52.67.94.32 18.230.109.192 18.229.199.232 3.212.79.116 3.92.113.229 34.193.91.42 34.237.40.31 3.215.10.168 34.236.228.98 3.214.203.147 3.208.110.31 100.26.2.217 3.215.143.88 18.119.73.75 3.136.153.91 3.128.101.143 35.166.246.78 35.161.40.209 54.149.249.153 35.161.32.231 52.34.65.236 35.163.245.143
Azure
Download Azure IP Addresses: JSON, CSV
Outbound requests from an app deployed to Azure will originate from one of the following IP addresses:
20.105.25.17 20.212.99.191 20.24.112.135 20.53.104.226 20.84.232.59 20.96.47.95 40.112.209.0 52.149.111.83
GCP
Download GCP IP Addresses: JSON, CSV
Outbound requests from an app deployed to GCP will originate from one of the following IP addresses:
34.150.239.218 34.69.118.121 34.78.133.163 34.82.246.143 34.93.58.231
Note
The above IP lists only apply to outgoing requests from Atlas Functions, including triggers and HTTPS endpoints that make outgoing requests.
For requests that originate from the Sync server, we recommend allowlisting the entire subnet of the App's Deployment Region and cloud provider. You can find the Deployment Region in the App Services UI under App Settings > General > Deployment Region.
DNS Filtering
You can use DNS filtering to specifically allow connections from client applications, including Device Sync clients, to the server.
Access *.services.cloud.mongodb.com via HTTPS or port 443.
Allowed Request Origins
You can define this configuration option in the
app-level root_config.json file. This field accepts an array of
URLs that incoming requests may originate from. If you define any allowed
request origins, then App Services blocks any incoming request from
an origin that is not listed.
IP Access List
App Services allows client requests from the enabled entries in the app's IP access list. Allowed requests will still use App Services's authentication and authorization rules. When you add IP access list entries, App Services blocks any request originating from an IP that is not on the access list.
Important
By default, any newly-created App allows access from any client IP by adding an access list entry for 0.0.0.0/0. If you delete this entry, no client can access your App from any IP address.
Find Your IP Address
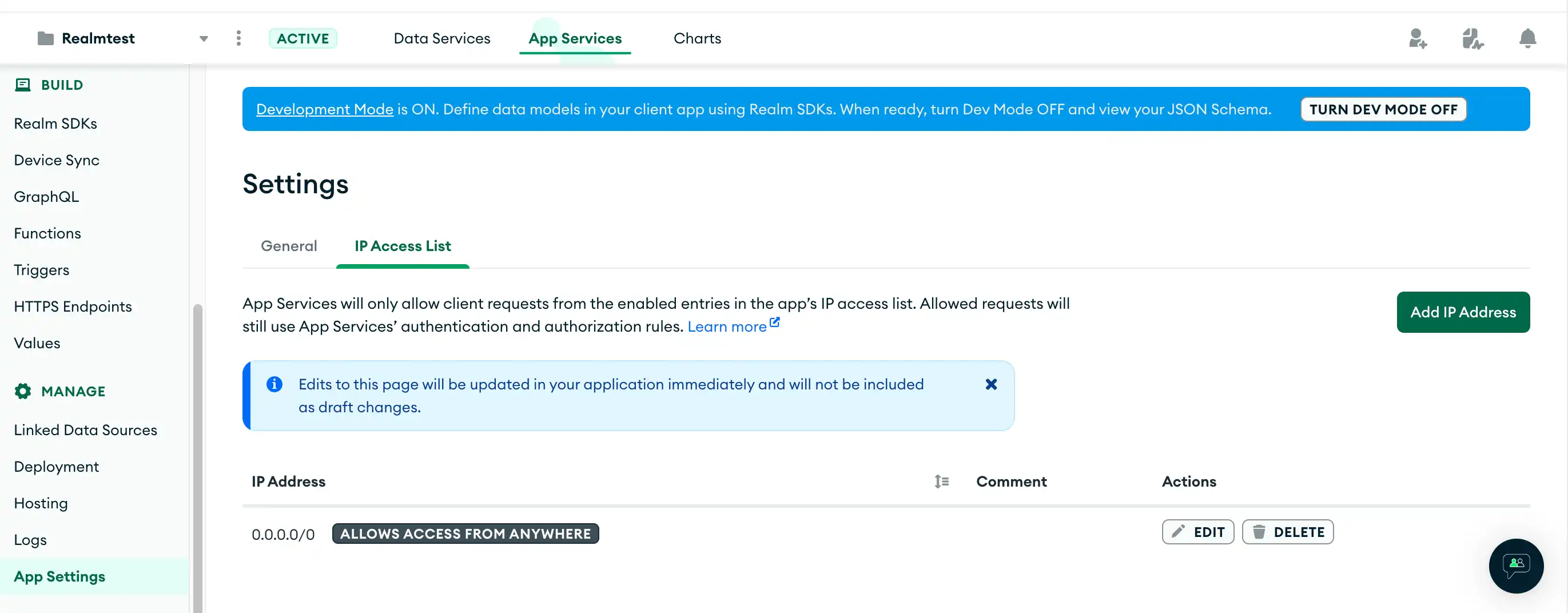
View IP Access List Entries
To view your IP Access List settings, navigate to App Settings in the App Services UI, and then click the IP Access List tab.
To view your IP access list entries, call appservices accessList list.
The CLI will then prompt you for your App ID.
To view your IP access list entries, create a GET request
in the following format. You must specify the Group and App ID.
curl --request GET \ --header 'Authorization: Bearer <access_token>' \ https://services.cloud.mongodb.com/api/admin/v3.0/groups/<groupId>/apps/<appId>/security/access_list
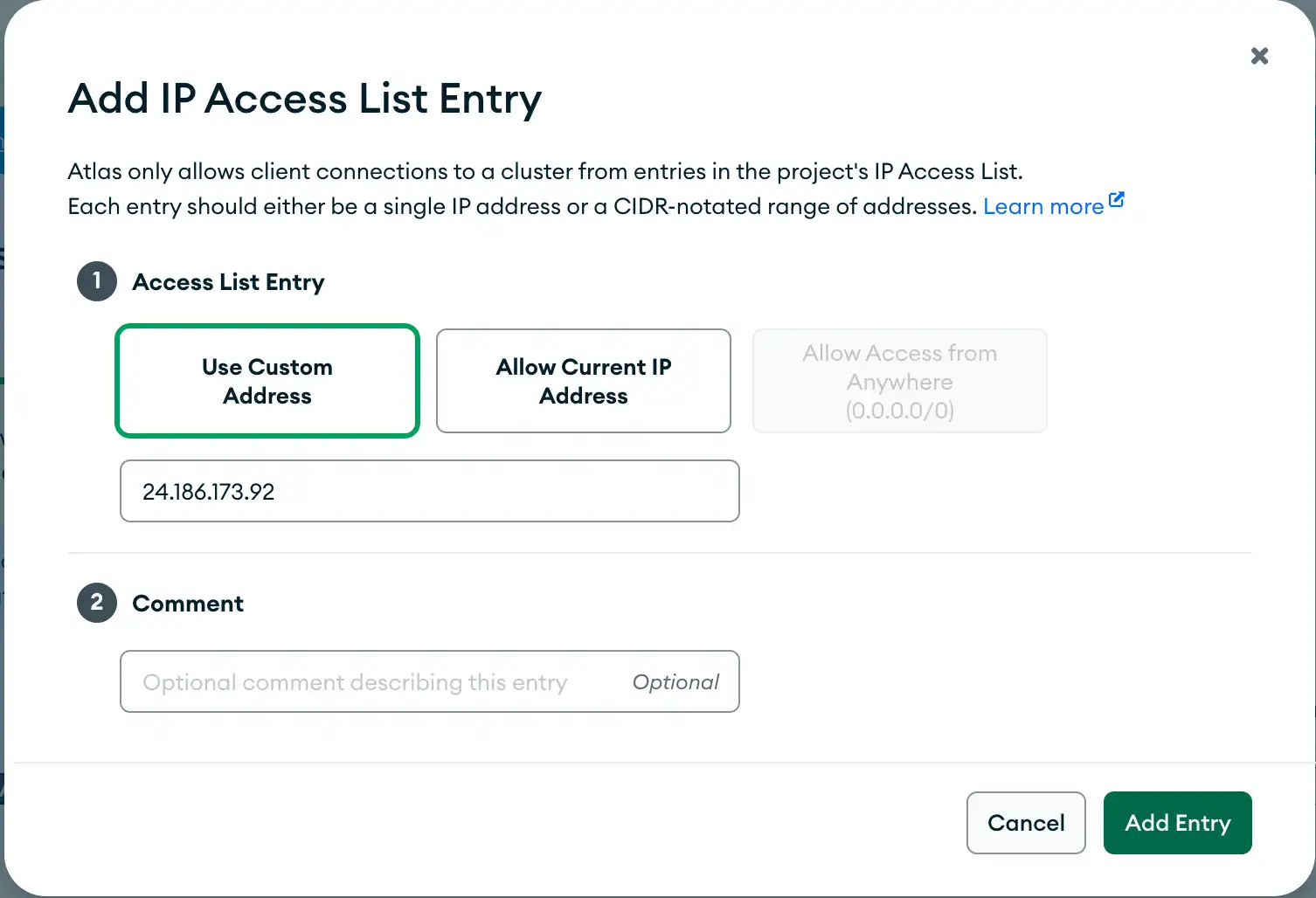
Create an IP Access List Entry
To add an IP address to the list of enabled entries, click the green Add IP address button to open the Add IP Access List Entry modal. This modal allows you to specify your current IP address or use a custom one. You can also specify a comment about the entry.
To create an IP access list entry, call appservices accessList create.
The CLI will prompt you to input an IP address and to select an App
from a list of all your Apps.
Optionally, you can specify any of the following arguments when you call the program:
appservices accessList create \ --app=<Your App ID> \ --ip=<IP Address> \ --comment=<Optional Comment> \ --use-current \ --allow-all
To create an IP access list entry, create a POST request
in the following format. You must specify the IP address in the request
body and the Group and App ID in the request URL.
curl --request POST \ --header 'Authorization: Bearer <access_token>' \ --data '{ "address": "<IP Address>" }' \ https://services.cloud.mongodb.com/api/admin/v3.0/groups/<groupId>/apps/<appId>/security/access_list
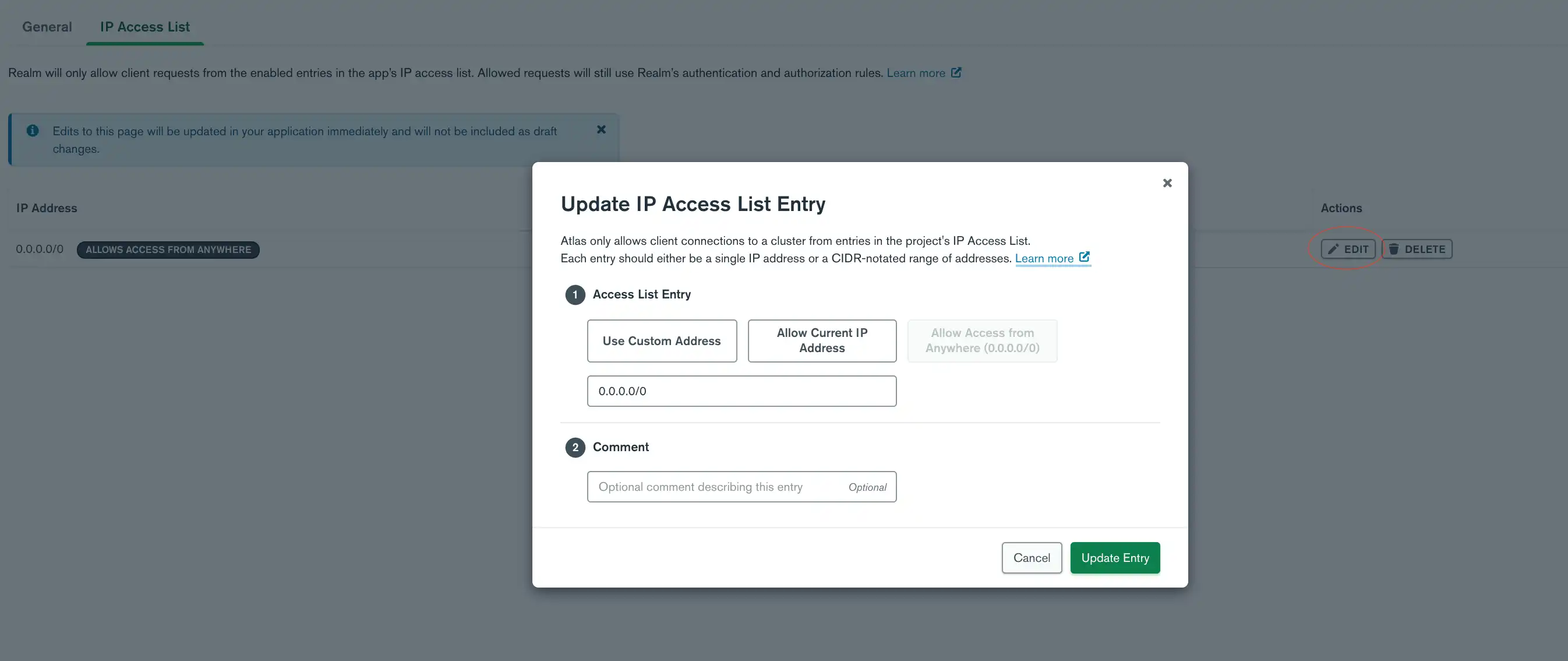
Edit an IP Access List Entry
To edit an entry, click the edit button on the right-hand side of the entry, and the Update IP Access List Entry modal will open. This modal allows you to specify your current IP address or use a custom one. You can also specify a comment about the entry.
You can edit an IP access list entry by updating the entry's IP address or by adding a comment to the entry. To update an entry's IP address, call:
``appservices accessList update --new-ip <IP Address>``
To add or update a comment, call:
``appservices accessList update --comment <Optional Comment>``
The CLI will then prompt you to select an App from a list of all your Apps and the IP address to update.
To update the IP address for an entry, create a PATCH request
in the following format. You must specify the new IP address in the request
body and the Group, App, and IP address ID in the request URL. The IP address
ID refers to the entry that you want to update. To get the ID for an IP address,
view your IP access list entries.
curl --request PATCH \ --header 'Authorization: Bearer <access_token>' \ --data '{ "address": "<IP Address>" }' \ https://services.cloud.mongodb.com/api/admin/v3.0/groups/<groupId>/apps/<appId>/security/access_list/<ipID>
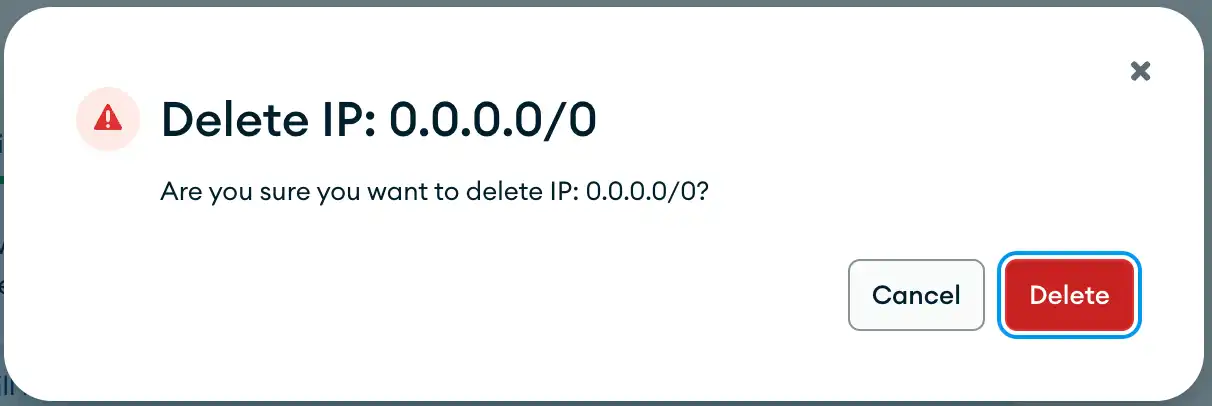
Delete an IP Access List Entry
To delete an entry, click the delete button on the right-hand side of the entry, and a modal will open requesting you to confirm that you want to delete the entry. Click the red delete button on the modal to complete the deletion of the entry.
To delete an IP access list entry, call appservices accessList delete.
The CLI will prompt you to input the App ID and to select which IP address
to delete.
To delete an IP access list entry, create a DELETE request
in the following format. You must specify the Group, App, and IP address ID.
To get the ID for an IP address, view your IP access list entries.
curl --request DELETE \ --header 'Authorization: Bearer <access_token>' \ https://services.cloud.mongodb.com/api/admin/v3.0/groups/<groupId>/apps/<appId>/security/access_list/<ipID>
API Access List
When you create an Atlas API key for project or organization access from the Realm CLI or the App Services Admin API, you can specify IP addresses that can use this API key. If you specify an IP address, App Services blocks any request originating from an IP address that is not on the access list.