As organizations look for ways to maximize resource efficiency while keeping pace with ever-evolving technology and customer expectations, the use of virtual machines (VMs) is increasing exponentially. In fact, virtual machine value across the United States experienced year-over-year growth of 11.8% to reach roughly $29 billion. The market is set to further expand at an impressive CAGR of 14.2% through 2033 (FMI, January 2023).
Understanding virtual machines is key for IT and business professionals alike as they become central to growth and IT strategies. Read on to enhance your understanding of virtual machines and virtualization, how virtual machines work, how virtual machines are used, and how to set up your own virtual machine.
What is a virtual machine?
A virtual machine (VM) is an application that functions as a virtual computer but resides within a physical computer (e.g., a host computer). Often referred to as guest machines, virtual machines work as separate independent machines but run as a process on the host machine's operating system. However, both the physical computer and the virtual machine believe they are each interacting with a separate physical machine. This is important because it keeps the host and guest machines from cannibalizing the other's resources, as well as enabling the use of guest operating systems by the VMs as they focus on specific tasks which are separate from the physical machine's functions.
How virtual machines work
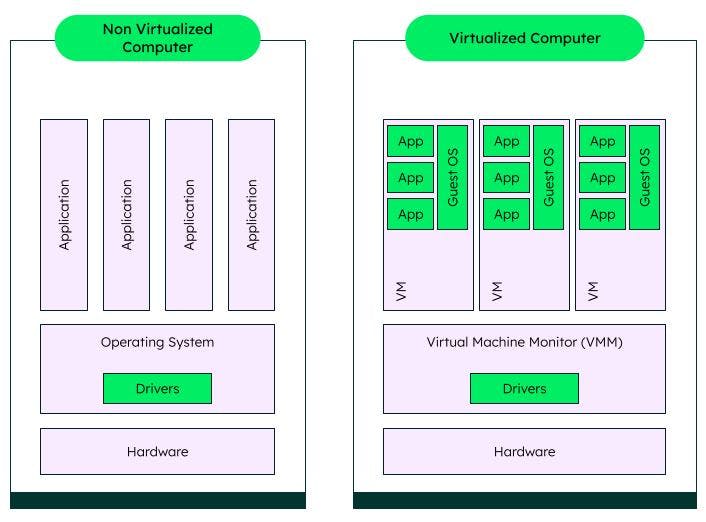
In the illustration below, a non-virtualized computer (e.g., physical machine) and a virtualized computer (e.g., virtual machine) are depicted.
To understand how virtual machines work, it's first necessary to understand the concept of virtualization and the different types of virtualization that are available.
What is virtualization and why is it important?
Virtualization is a process where software is used to create an abstraction layer (the decoupling of the operating system from the physical hardware platform and applications that run on it). This is the basis of cloud computing, enabling the creation of virtual resources such as virtual servers, desktops, operating systems, files, storage, and networks.
In the illustration above, the non-virtualized computer's single operating system with its drivers is in direct connection or relationship with the physical machine's hardware, and individual apps then utilize the single operating system. However, in the virtualized computer, the hardware and operating systems used by applications are separated by the Virtual Machine Monitor (VMM) software. VMM software enables the creation, management, and governance of virtual machines and manages the operation of a virtualized environment on top of a physical host machine (Technopedia, 2023).
It's important to note that when discussing virtual machines, it's common to refer to an entire computer being virtualized, but many components can be individually virtualized as well.
Different types of virtualization
There are many types of virtualization, including application, desktop, network, hardware, storage, data, data center, GPU, Linux, and cloud virtualization. For the purposes of this discussion, the following types of virtualization are most relevant.
Application virtualization
Hypervisor software, working in conjunction with VMM software, acts as the interface between virtual resources and the underlying physical hardware. Hypervisors not only ensure that each virtual resource has access to the physical resources it needs, but also keep virtual resources from interfering with each other by taking resources from each other or otherwise interrupting computing cycles. It's also important to note that there are two types of hypervisors.
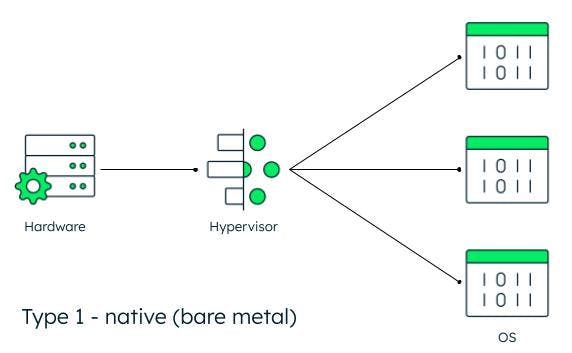
- Type 1 hypervisor: Type 1 hypervisors are sometimes referred to as bare-metal hypervisors because they run directly on the physical machine and have access to all of the physical computer's resources. Bare-metal hypervisors are very efficient and are often used in server virtualization, desktop virtualization, and app virtual environment creation. Another attribute of Type 1 hypervisors is that they may be kernel-based virtual machine(s) (KVM), meaning they contain their own kernel, as opposed to Type 2 hypervisors, which do not.
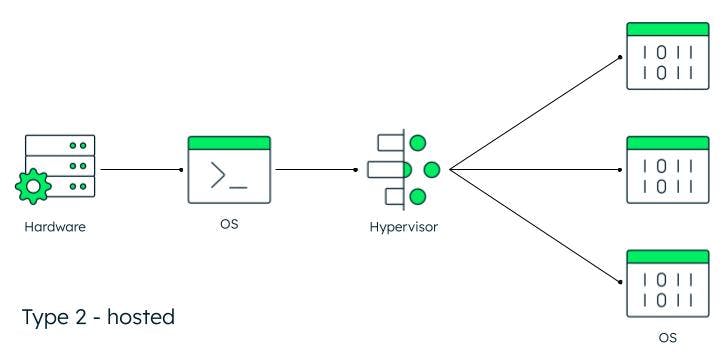
- Type 2 hypervisor: Type 2 hypervisors, or hosted hypervisors, are installed on a host machine that already has its own operating system (OS) running. This pre-existing OS is in charge of resource allocation, and the hosted hypervisor will only focus on the environment created for a specific function or task. For example, hosted hypervisors are often used to create virtual environments where developers can build and test applications.
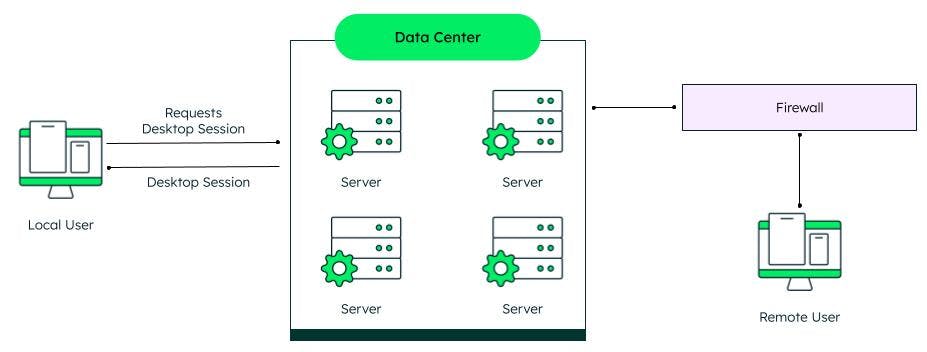
Desktop virtualization
Desktop virtualization enables multiple desktop operating systems — each in its own virtual machine on the same computer. This type of virtualization enables many lightweight desktops to run on a shared physical machine which provides more user productivity with less hardware and maintenance.
Hardware virtualization
Hardware virtualization enables physical hardware to be treated as separate virtual devices that can be accessed over a network. One example includes CPU virtualization, which makes hypervisors, virtual machines, and guest operating systems possible. It allows a single CPU to be divided into multiple virtual CPUs for use by multiple virtual machines.
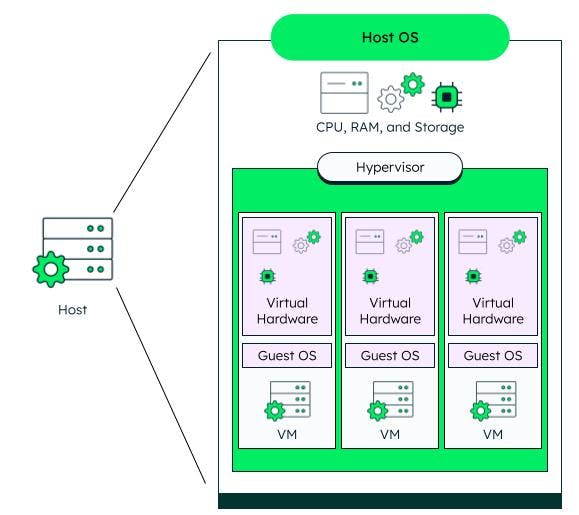
Storage virtualization
Disk space can be split up into smaller pieces dedicated to a virtual machine. In the same vein, a server can also combine virtual storage spaces to create much larger virtual disks.
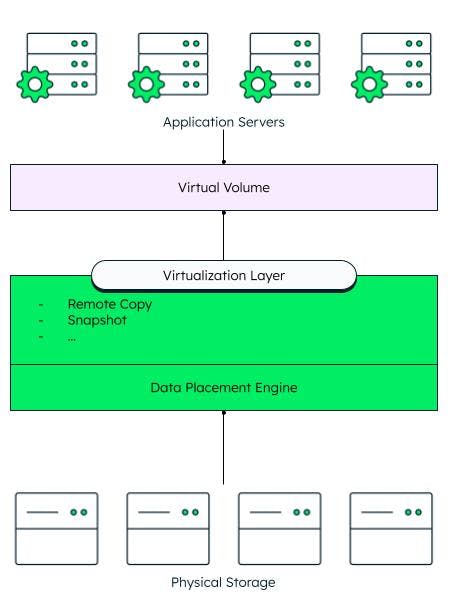
Network virtualization
Virtual sub-networks can be created in a software network. These networks can be used to route traffic across different resources in an extensive infrastructure.
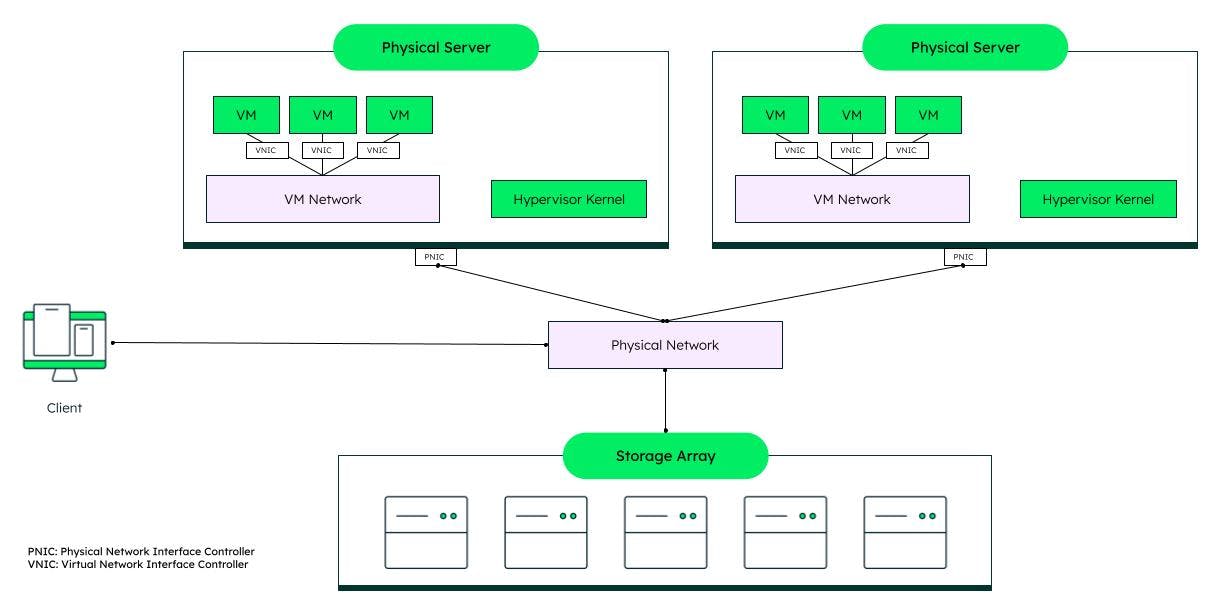
Note that in the diagram above, each VM network provides connectivity to a hypervisor kernel. This indicates that the hypervisor being used in our example is a Type 2 hypervisor, as it is not a KVM.
How virtual machines are used
Virtual machines are used to dedicate a portion of a host computer's resources to a specific task. Running in an isolated environment without any risk of conflicting with the host computer allows additional resource focus on a specific process or task without slowing down host computer processing or interrupting host computer cycles. And, if the guest virtual machine crashes, it can be rebooted or recovered without impacting the host computer as well.
Given these attributes, it's not surprising organizations are relying more and more heavily on virtual machine work to extract more productivity from every single physical computer. Here are some of the most common ways virtual machines are used.
Common ways virtual machines are used
- Consolidation
Organizations often use virtual machines to host multiple VMs using a single physical server. This significantly reduces the need to distribute workloads across multiple servers, which is costly and inefficient from both an administration and resource standpoint.
- Scaling flexibility
Through the use of virtualization software, organizations can extend computing resources, enabling flexibility in their workload and traffic support resources. Specifically, instead of buying additional hardware to support fluctuating workloads, a single physical machine can be virtualized to contain multiple VMs that can pick up the slack when needed. Some examples of virtual machine software include Microsoft Hyper-V, IBM Power VM, Oracle VM, and Java Virtual Machine.
- Enhanced cybersecurity
In the event of a cyberattack, if a physical host computer is infected with a virus by accessing virus-infected data, the damage can be significant. However, if one virtual machine is infected, that virtual machine can simply be deleted quickly, minimizing damage and risk of exposure to other physical and virtual environment entities. In addition, restoring a VM to the most recent backup is a far less tedious and time-consuming process than restoring a real computer machine.
- Support of multiple operating systems
With a physical computer, there is one host operating system. As a result, software, tasks, and administration are bound by the constraints of that host operating system. However, with the use of multiple virtual machines, different operating systems (e.g., guest operating systems or virtual operating systems) can be run on the same physical computer. Here are some examples of how running a different operating system as a virtual or guest operating system versus the host operating system can be beneficial.
- Legacy system support:
When an organization's older operating systems support crucial legacy systems that, due to cost or effort, an organization is reticent to replace, the use of different operating systems via VMs can be advantageous. Specifically, by having new virtual machines run up-to-date operating systems, newer versions of technology and associated software can be utilized without removing the older OS that is supporting internal legacy systems.
- Operating system migration:
Whether an organization is migrating physical resources to cloud environments, transitioning functions to cloud computing, or implementing a new operating system, creating a new operating system virtual machine can ease the transition risk and give developers the time and space to test the new system without full integration into the physical machines and underlying hardware. In addition, as mentioned above, legacy systems will not be impacted as the host operating system remains untouched until it's time for full migration.
Different types of virtual machines
There are two basic types of virtual machines. They are system virtual machines and process virtual machines.
System virtual machine: System VMs accommodate an OS being completely installed. This enables multiple virtual machines to run different operating systems than the host machine.
Process virtual machine: Process VMs focus on application functionality and do not allow the complete installation of an OS. Instead, they create a virtual environment of an OS while running a specific app or program, and then will destroy the OS environment when the app or program is closed.
Setting up a virtual machine
There are many ways to go about setting up a VM. However, before getting started, it's important to ask some basic questions to create a VM plan.
What is the primary anticipated use for your VM, and which type of VM will you be building (e.g., system or process)?
What resources will your VM need (e.g., memory, storage)?
What type of connectivity or access to other VMs or applications will your VM require?
Will you be building your own VM, or is it more practical to use the ready VM wizards available with most cloud providers?
How will cybersecurity and backup be addressed for your VM?
Once you have a basic VM plan, it's time to get started. For their first VM build, most people take advantage of their cloud provider's VM wizard. In doing so, building a VM is quickly completed using the following steps.
Locate the Cloud Engine in your cloud provider's platform.
Select the "Create" tab or window and answer the questions posed regarding your VM requirements. Be aware that some of the choices you make cannot be changed (e.g., physical location) so consider your answers carefully before entering them.
Likely questions you'll encounter include:
a. What is your VM's name?
b. What is your VM's physical location?
c. What type of VM are you building (e.g., general purpose or memory optimized)?
d. Will you be using containers in your VM?
e. Which OS will your VM use?
f. What types of access are you seeking for your VM (e.g., APIs, firewalls, user access)?
- When you are satisfied with all your answers, click on the create button and your new VM should appear in your cloud provider platform window.
If you would instead prefer to run a virtual machine on your personal computer, many software applications, such as VirtualBox, can help you set up and run virtual machines as well.
FAQs
What is a virtual machine (VM)?
What is virtualization?
What are the different types of virtualization?
What is a hypervisor?
What is a virtual machine used for?
Virtual machines can be used to combine multiple hardware resources into one virtual resource on a single physical machine or server. This can streamline administration, improve efficiency, and reduce costs while increasing scalability and performance. Some additional uses for VMs include:
Running multiple operating systems simultaneously
Consolidating various applications within one cybersecurity environment to increase security while decreasing administrative time and costs
Accessing suspected virus-infected data or other malware-impacted files in an enclosed, safe environment
Acting as a test environment for patches, upgrades, and potential configuration changes
Running outdated, legacy software that is no longer compatible with new operating systems (OSs) or environments
What is an example of a Virtual Machine (VM)?
Many people use virtual machines (VMs) every day without even realizing it. For example, every time Microsoft Office 365, Google Workspace, or popular online storage services are accessed, the user is actually interacting with these applications through a web interface supported by a virtualized backend infrastructure (e.g., VMs).
Another example involves emulation where a user is running an Android app in an Apple iOS environment or vice versa. While users may be aware that they're running Android apps on their computers or Internet of Things (IoT) devices they may not realize that emulation technology, which involves virtualization created via VMs, is being used.
From a more technical perspective, "actual" VMs (e.g., the software needed to create/use VMs) are available from a variety of sources. Some of the most commonly used include:
- VMware
- Oracle VM VirtualBox
- Microsoft Azure (VM)
- Citrix Workspace App
- Parallels Desktop
There are also a variety of open-source applications to help create VMs as well.
Is it legal to use a Virtual Machine (VM)?
It is perfectly legal to use a virtual machine. With that said, VM developers can run into legal issues in some of the following situations:
Licensing: When running operating systems (OSs) on your physical computer, you are required to have a license from the owner (e.g., Microsoft, Apple) or designated reseller of that OS. However, possessing a single OS license and running it on both a physical computer and a VM can constitute a legal issue. Either a license allowing for multiple OS instantiations or two individual licenses would be required in this situation.
Apple restrictions: Apple does not allow the installation of macOS on non-apple machines, devices, etc. This means that if a developer is running a VM that runs macOS, the host computer of that VM must also be running macOS, and presumably be an approved combination of Apple product hardware and software.